Introduction
When we look at the fabric of modern digital systems, the concept of the software supply chain extends far beyond third-party libraries and open-source components. It encompasses the people, processes, and technologies that collectively contribute to the development and deployment of modern systems and applications. This includes not only external dependencies but also the intricate interactions between various teams within an organisation — developers, testers, security and operations — and the systems they use, such as Continuous Integration/Continuous Deployment (CI/CD) pipelines and cloud services.
Securing the software supply chain has become a critical priority, highlighted by recent high-profile incidents that exposed vulnerabilities not just in code, but in processes and technologies. These events underscore the need to adopt a holistic approach to supply chain security, addressing risks associated with people, and process, as well as technology. The integration of Artificial Intelligence (AI) and Large Language Models (LLMs) into the supply chain presents both new threats and significant opportunities. AI and LLMs can be used by attackers to automate and scale sophisticated cyber-attacks, create realistic phishing scams, and exploit vulnerabilities with unprecedented speed. Conversely, they also empower defenders with enhanced threat detection, predictive analytics, and automated responses, helping to identify and mitigate risks more effectively.
This article aims to broaden the concept of supply chain security by examining these three crucial aspects. We will explore how the interactions between teams, the workflows they follow, and the technologies they employ can introduce risks at various stages of the supply chain. By understanding these risks and implementing comprehensive security measures, organisations can better protect their systems and data from potential threats.
Whether you’re a seasoned software architect or a security professional, this article will provide you with insights and best practices to enhance your supply chain security. We will delve into the key components and stages of the software supply chain, explore potential internal and external threats, including those posed by AI and LLMs, and discuss actionable steps to mitigate these risks.
With this overview in mind, let’s begin our journey into securing the software supply chain by examining the critical intersections of people, process, and technology.
Expanding our Understanding of the Software Supply Chain
The software supply chain is an intricate and essential component of modern software development and deployment. It goes beyond just the code and libraries to include the people, processes, and technologies that work together to bring software from conception to production. This expanded view allows us to better understand the multifaceted nature of supply chain security and the various points where vulnerabilities can arise.
Definition of the Software Supply Chain in the SDLC
Traditionally, the software development lifecycle is seen as a series of steps and components involved in developing, building, testing, and deploying software. The SDLC supply chain includes third-party libraries, open-source components, proprietary software, and hardware. However, a comprehensive approach broadens this definition to encompass the human and procedural elements that are integral to the use of these technical components.
Key Components
- Third-Party Libraries and Frameworks
- These are pre-written code libraries or frameworks that developers use to accelerate development. They come with inherent risks, including potential vulnerabilities and malicious code.
- The suppliers are also subject to supply chain risks of their own, and a compromise of upstream supply chains poses a direct risk to the consumers of these libraries and frameworks.
- Open-Source Components
- Widely used due to their flexibility and cost-effectiveness, open-source components are a double-edged sword, offering both innovation and potential security risks from unvetted contributions.
- Proprietary Software
- Internally developed software that, while more controlled, can still pose direct and indirect risks to the systems and processes involved in software delivery.
- Considerations of “Build vs Buy” for internal tooling have to balance the internal supply chain risks of building in-house against the risks posed by onboarding a supplier.
- Hardware
- Physical devices and infrastructure that support software operations, can be vulnerable to supply chain attacks at the manufacturing or distribution stages.
- BYOD policies can amplify or introduce risk by allowing personal hardware to access data, code, and tooling that has not been under the same scrutiny as company issued devices.
- Inter-Team Interactions
- Effective collaboration and communication between development, testing, security, and operations teams are crucial. Miscommunication or siloed operations can lead to security oversights and process inefficiencies.
- Systems and Tools
- Continuous Integration/Continuous Deployment (CI/CD) pipelines, cloud services, and other automation tools streamline development and deployment but also introduce risks if not properly secured.
- Architecture and Design of Software
- The initial design and architecture of the software play a critical role in determining its security posture. Poor design choices can introduce vulnerabilities that are difficult to mitigate later in the development cycle. Secure design principles, threat modeling, and architecture reviews are essential to building robust software.
- Enterprise Architecture
- The broader enterprise architecture, including network design, data flow, and integration points, impacts the overall security of the software supply chain. A well-architected enterprise environment supports secure software development and deployment by incorporating security best practices into the infrastructure and workflows.
The Interconnectedness and Complexity
The modern software supply chain is a complex, interconnected web where the failure or compromise of one component can have cascading effects. For example, a vulnerability in a widely-used open-source library can affect multiple projects and organisations. Similarly, poor communication between development and operations teams can result in misconfigured systems that are vulnerable to attacks.
Understanding this complexity is crucial for identifying where risks might emerge and implementing strategies to mitigate them. It requires a holistic approach that considers technical, human, and procedural factors throughout the SDLC, ensuring that all aspects of the supply chain are robust and secure.
With this understanding of the expanded software supply chain, we can now explore the specific stages of this chain and the associated risks in greater detail. Let’s move on to the stages of the software supply chain and the best practices to secure each stage.
The Software Development Lifecycle and Associated Supply Chain Risks
The software development lifecycle encompasses various stages, each with its own set of supply chain risks. By understanding these stages, organisations can implement targeted security measures to protect their systems. Engineering leaders should work with Security to look closely at their SDLC, and seek to understand the risks at each stage.
Here are some examples at each stage of the SDLC.
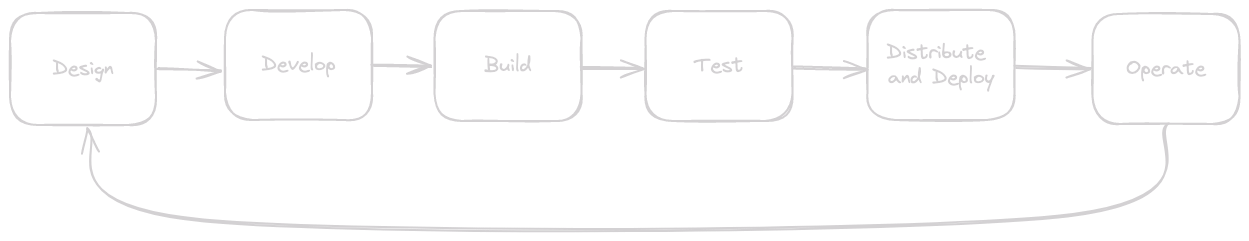
- Design
- Components: Architecture, Technology Selection, Requirements, and Standards
- Risks: Improper Design, Conflicting Priorities, Inappropriate Technology Choices.
- Best Practices:
- Industry best practices for solutions architectures
- Peer reviewed architecture and feature designs
- Strong Security culture throughout engineering organisations.
- Threat Modelling and Risk management processes
- Development
- Components: Use of third-party libraries, frameworks, and proprietary code.
- Risks: Vulnerable code, malicious code injection, poor communication.
- Best Practices:
- Conduct thorough code reviews and static analysis.
- Implement dependency management tools.
- Foster effective communication protocols among team members.
- Build and Integration
- Components: CI/CD pipelines, build tools.
- Risks: Compromised build tools, misconfigurations, malicious build scripts.
- Best Practices:
- Secure CI/CD pipeline configurations.
- Use signed artifacts and verify integrity.
- Ensure cross-team coordination to prevent misconfigurations.
- Testing
- Components: Automated and manual testing processes.
- Risks: Unsecure test environments, exposure of sensitive data, inadequate testing coverage.
- Best Practices:
- Use isolated test environments.
- Anonymize test data to protect sensitive information.
- Develop comprehensive test plans to cover all potential vulnerabilities.
- Distribution
- Components: Cloud repositories, software registries.
- Risks: Repository compromises, tampered packages, insecure distribution channels.
- Best Practices:
- Verify checksums and use signed packages.
- Employ secure distribution practices.
- Establish clear distribution protocols to ensure integrity.
- Maintain a verified cache of package dependencies to ensure availability and limit opportunities for tampering.
- Deployment
- Components: Production environments, deployment tools.
- Risks: Deployment of compromised software, insecure configurations, rushed deployments.
- Best Practices:
- Validate deployments through rigorous checks.
- Implement configuration management practices.
- Monitor deployments and use staged rollouts to mitigate risks.
- Maintenance and Updates
- Components: Software updates, patch management.
- Risks: Update hijacking, delayed patching, insufficient update processes.
- Best Practices:
- Automate updates where possible and ensure timely patching.
- Develop and follow robust patch management policies.
- Regularly review and update maintenance processes to address new vulnerabilities.
By understanding and securing each stage of the software supply chain, organisations can significantly reduce their risk exposure. This requires a strategically concerted effort to address not only technical vulnerabilities, but also the processes and people involved across the engineering domain. Understanding these risks and implementing best practices is essential for a holistic approach to supply chain security.
We’ll delve more into each stage further in future articles, where we will expand on the best practices to provide examples of each to support the continuous improvement of your supply chain security.
Next, we’ll explore some internal and external threats to the supply chain and the strategies to mitigate these threats. You can be sure that this list isn’t comprehensive, it is merely a dip into the issue to provide some idea of the threats that exist.
Internal and External Threats to the Supply Chain
Understanding the threats that can impact the software supply chain is crucial for developing effective security strategies. These threats can originate from both internal and external sources, each presenting unique challenges and risks. With the emergence of Artificial Intelligence (AI) and Large Language Models (LLMs), new threat vectors have also come into play, further complicating the security landscape.
Internal Threats
1. Insider Threats
- Risks: Malicious insiders, negligent employees.
- Mitigation Strategies:
- Implement strict access controls and least privilege principles.
- Conduct regular security training to raise awareness among employees.
- Monitor and analyze user activities to detect anomalous behavior.
- Establish clear policies and consequences for violations to deter malicious actions.
2. Process-Related Risks
- Risks: Communication breakdowns, process gaps, inefficient workflows.
- Mitigation Strategies:
- Develop and enforce standardized communication protocols across teams.
- Conduct regular process audits to identify and address gaps.
- Promote a culture of collaboration and continuous improvement.
- Utilize project management tools to streamline workflows and improve coordination.
3. AI and LLM-Related Risks
- Risks: Misuse of AI tools by insiders, unintentional bias in AI models, over-reliance on AI-generated code.
- Mitigation Strategies:
- Restrict access to AI and LLM tools to authorized personnel.
- Provide training on the ethical use of AI and the importance of avoiding biases.
- Regularly audit AI models for biases and inaccuracies.
- Validate AI-generated code through manual reviews and testing to ensure quality and security.
External Threats
1. External Attackers
- Risks: Nation-state actors, cybercriminals targeting supply chain vulnerabilities.
- Mitigation Strategies:
- Implement robust perimeter defenses, including firewalls and intrusion detection systems.
- Regularly update and patch all software and systems to close known vulnerabilities.
- Use threat intelligence services to stay informed about emerging threats.
- Employ multi-factor authentication (MFA) to secure access to critical systems.
2. Attacks against your Supply Chain
- Risks: Compromise of third-party components, Supplier Compromise, watering hole attacks.
- Mitigation Strategies:
- Conduct thorough vetting and continuous monitoring of third-party vendors.
- Use signed and verified components to ensure integrity.
- Implement network segmentation to limit the impact of a potential breach, consider architectural patterns such as Zero Trust.
- Develop an incident response plan specifically tailored to supply chain attacks.
3. AI and LLM-Related Threats
- Risks: Adversarial attacks on AI models, exploitation of AI-generated vulnerabilities, automated spear-phishing attacks.
- Mitigation Strategies:
- Implement robust security measures for AI models, including adversarial training.
- Regularly test AI systems for vulnerabilities and address any identified issues promptly.
- Use AI and ML-based security tools to detect and mitigate automated threats.
- Educate employees about the risks of AI-powered social engineering attacks and how to recognize them.
By understanding and addressing these internal and external threats, including those posed by the emergence of AI and LLMs, organisations can build a more resilient supply chain. This involves not only implementing technical controls but also fostering a security-conscious culture and maintaining vigilant oversight of all supply chain activities.
In the final section, we will recap the key points and discuss the importance of a holistic approach to supply chain security, providing actionable steps to enhance your organisation’s defenses.
Conclusion
Securing the software supply chain requires a holistic approach that addresses the technical, human, and procedural aspects of development and deployment. The integration of AI and Large Language Models (LLMs) adds a new dimension to this challenge, offering both risks and opportunities for attackers and defenders alike. Let’s recap the key points and discuss actionable steps to enhance your organisation’s supply chain security.
Recap of Key Points
-
Expanded Scope of the Software Supply Chain
- Beyond third-party libraries and open-source components, the supply chain includes people, processes, and technology.
- Your organisation is both a Consumer and producer within the supply chain. Your approach should look to protect you from upstream threats (Suppliers and Third-Parties), but also protect those downstream (Customers, Clients, Consumers) if you were to be attacked.
- Key components include third-party libraries, open-source components, proprietary software, hardware, inter-team interactions, systems like CI/CD pipelines, and the architecture of both software and the enterprise.
-
Stages of the Software Development Lifecycle and Associated Supply Chain Risks
- Take a strategic view of your SDLC, understand each stage and how to protect it, but also how those protections cascade to future stages.
- Each stage, from design and development to maintenance and updates, has its unique risks.
- Regularly review and look to implement best practices for securing each stage include thorough code reviews, secure configurations, comprehensive testing, secure distribution practices, deployment validation, and automated updates.
-
Internal and External Threats
- Internal threats include insider threats, process-related risks, and AI-related risks such as misuse of AI tools and unintentional bias.
- External threats include direct external attackers, attacks against your supply chain, and AI-related threats such as adversarial attacks on AI models and automated spear-phishing attacks.
-
Impact of AI and LLMs
- For Attackers: AI can be used to automate attacks, create more sophisticated social engineering schemes, and exploit vulnerabilities at scale.
- For Defenders: AI can enhance threat detection, automate responses, and improve the overall security posture through predictive analytics and continuous monitoring.
Importance of a Holistic Approach
Securing the supply chain is not just about implementing technical controls; it’s about creating a culture of security and continuous improvement. This includes:
- People: Ensuring that all team members are aware of security best practices and understand the importance of their role in protecting the supply chain.
- Processes: Establishing robust processes that include regular audits, clear communication protocols, and comprehensive risk management strategies.
- Technology: Leveraging advanced tools and technologies, including AI and ML, to enhance security measures and stay ahead of emerging threats.
Actionable Steps to Enhance Supply Chain Security
-
Conduct Comprehensive Risk Assessments
- Regularly evaluate the entire supply chain to identify and mitigate potential vulnerabilities.
-
Implement Robust Access Controls
- Use the principle of least privilege to limit access to sensitive systems and data.
-
Foster a Security-Conscious Culture
- Provide ongoing training and resources to ensure all employees understand their role in supply chain security.
-
Leverage AI and ML Tools
- Use AI-based tools for threat detection, anomaly detection, and automated response to enhance your security capabilities.
-
Stay Informed About Emerging Threats
- Continuously monitor the threat landscape and update your security measures to address new vulnerabilities and attack vectors.
-
Develop and Maintain an Incident Response Plan
- Ensure you have a clear plan in place to respond quickly and effectively to any supply chain security incidents.
-
Be Aware of Downstream Implications
- Remember that if your supply chain is compromised, you may unwittingly contribute to the compromise of someone downstream. Ensuring robust security practices protects not only your organisation but also your partners and clients.
By taking these steps, organisations can significantly enhance their supply chain security and build resilience against both current and future threats. This proactive approach is essential for protecting your systems, data, and reputation in an increasingly complex and interconnected digital world. No one person or company is an island, everyone has a dependency on someone or something else, by understanding where you sit as a link in the wider supply chain you can contribute to improving the security of the digital world for everyone.
A Call to Action
As we navigate the evolving landscape of supply chain security, it is crucial to remain vigilant and proactive. Evaluate your own supply chain security across all dimensions — people, processes, and technology — both up and downstream. Consider implementing some of the best practices discussed in this article. Remember, if your supply chain is compromised, you may unwittingly contribute to the compromise of someone downstream. For further reading and tools, explore the resources provided below.
Reference Materials for Supply Chain Security
Here are some valuable resources and guidelines from NIST, the UK National Cyber Security Centre (NCSC), and other authoritative sources to help you enhance your understanding and implementation of supply chain security:
NIST Resources
-
NIST Special Publication 800-161 Revision 1:
- This publication provides comprehensive guidance on cybersecurity supply chain risk management (C-SCRM). It covers identifying, assessing, and mitigating risks throughout the supply chain at all organisational levels.
- Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations
-
Executive Order 14028 Guidance:
- Following the executive order on improving the nation’s cybersecurity, NIST has developed guidelines to enhance software supply chain security. This includes criteria for evaluating software security and secure practices for developers and suppliers.
- Software Supply Chain Security Guidance
-
Defending Against Software Supply Chain Attacks:
- Co-released by CISA and NIST, this resource provides strategies and best practices to defend against software supply chain attacks. It includes recommendations for using the C-SCRM framework and Secure Software Development Framework (SSDF).
- Defending Against Software Supply Chain Attacks
-
NIST Cyber Supply Chain Risk Management (C-SCRM) Program:
- This program provides ongoing research, resources, and stakeholder engagement to help organisations manage supply chain risks. It includes foundational and enterprise-wide practices for effective risk management.
- Cybersecurity Supply Chain Risk Management
NCSC Resources
-
Supply Chain Security Collection:
- The NCSC offers a comprehensive collection of guidance documents focused on supply chain security. These resources provide practical advice on managing supply chain risks, including principles for maintaining control over the supply chain and steps to improve organisational cyber resilience.
- Supply Chain Security Guidance
-
Assessing Supply Chain Cyber Security:
- This guidance helps organisations assess the cyber security of their supply chains. It covers establishing a risk management approach, involving key stakeholders, and creating repeatable processes for supplier assessment.
- Assess Supply Chain Cyber Security
-
Principles for Supply Chain Security:
- The NCSC outlines 12 principles designed to help organisations gain and maintain control over their supply chains. These principles cover aspects such as understanding supply chain dependencies, establishing effective communication channels, and ensuring continuous improvement.
- Principles for Supply Chain Security
-
Supply Chain Mapping Recommendations:
- The NCSC provides recommendations for mapping supply chain dependencies to better anticipate and mitigate cyber risks. This guidance helps organisations identify critical supply chain components and assess their vulnerabilities.
- Supply Chain Mapping Recommendations